In this tutorial, we’ll walk through the process of enabling Multi-Factor Authentication (MFA) using the Time-based One-Time Password (TOTP) method in HashiCorp Vault. Implementing MFA enhances the security of your Vault server by adding an additional layer of authentication.
Prerequisites
Before we begin, ensure that you have a working installation of HashiCorp Vault on Ubuntu. If you haven’t installed Vault yet, follow these steps to get started:
Installing Vault on Ubuntu
Update and Upgrade Your System:
sudo apt-get update && sudo apt-get upgrade -yInstall Required Tools:
sudo apt install net-toolsDownload and Install Vault:
wget -O- https://apt.releases.hashicorp.com/gpg | sudo gpg --dearmor -o /usr/share/keyrings/hashicorp-archive-keyring.gpg
echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/hashicorp.list
sudo apt update && sudo apt install vaultStart and Enable Vault Service:
sudo systemctl daemon-reload
sudo systemctl start vault
sudo systemctl enable vault
sudo systemctl status vaultGo to the browser and open the http://ip-address:8200 you will have to enter the key shares and key threshold. After adding this you will get the vault root token and keys.
With Vault installed and running, let’s proceed to configure MFA using the TOTP method.
Configuring MFA Using TOTP in Vault
Here is the step by step guide to enable the MFA using TOTP method in the Hashicorp Vault server.
Set Vault Environment Variables:
export VAULT_TOKEN=vault-token
export VAULT_ADDR=http://localhost:8200Enable the Userpass Authentication Method:
vault auth enable userpassRetrieve the Userpass Auth Accessor:
USERPASS_ACCESSOR=$(vault auth list | grep userpass | awk '{print $3}')Create a New User in Vault:
Replace demo with your desired username and $MY_PASSWORD with the user’s password:
vault write auth/userpass/users/demo password=your-passwordCreate an Identity Entity and Alias:
ENTITY_ID=$(vault write -field=id identity/entity name="demo")vault write identity/entity-alias name="demo" canonical_id="$ENTITY_ID" mount_accessor="$USERPASS_ACCESSOR"Create a TOTP MFA Method:
METHOD_ID=$(vault write -field=method_id identity/mfa/method/totp issuer=HCP-Vault period=30 key_size=30 qr_size=200 algorithm=SHA256 digits=6 name=demo)This command will generate a method ID for the TOTP MFA setup.
Generate and Retrieve TOTP Barcode URL:
vault write identity/mfa/method/totp/demo-generate method_id=$METHOD_ID entity_id=$ENTITY_IDThis will generate the Barcode and the URL.
Key Value
--- -----
barcode iVBORw0KGgoAAAANSUhEUgAAAMgAAADIEAAAAADYoy0BAAAG50lEQVR4nOydwW7kOAxEN4v5/1+ePXgPGhAsPIoOptKodwpsWVJ3gQRJsZ1fv3//E4z4929vIPxJBDEjgpgRQcyIIGZEEDMiiBkRxIwIYkYEMSOCmBFBzIggZkQQMyKIGRHEjAhiRgQxI4KY8YsO/PqiI89T+vOp5/pzhZzk1xXrDHX+OkO3lp6f7PnuO9HEQsyIIGZgl
url otpauth://totp/HCP-Vault:8467fcb6-7e64-39ae-c992-0c33da5b87d3?algorithm=SHA256&digits=6&issuer=HCP-Vault&period=30&secret=LJD2KTFDEXZWOTELLW366OR7FE5XZNVUse the URL provided to generate a barcode. You can use the following website to create the barcode:
QR Code Generator
Use this Link to generate the barcode using the URL generated in above step. https://stefansundin.github.io/2fa-qr/
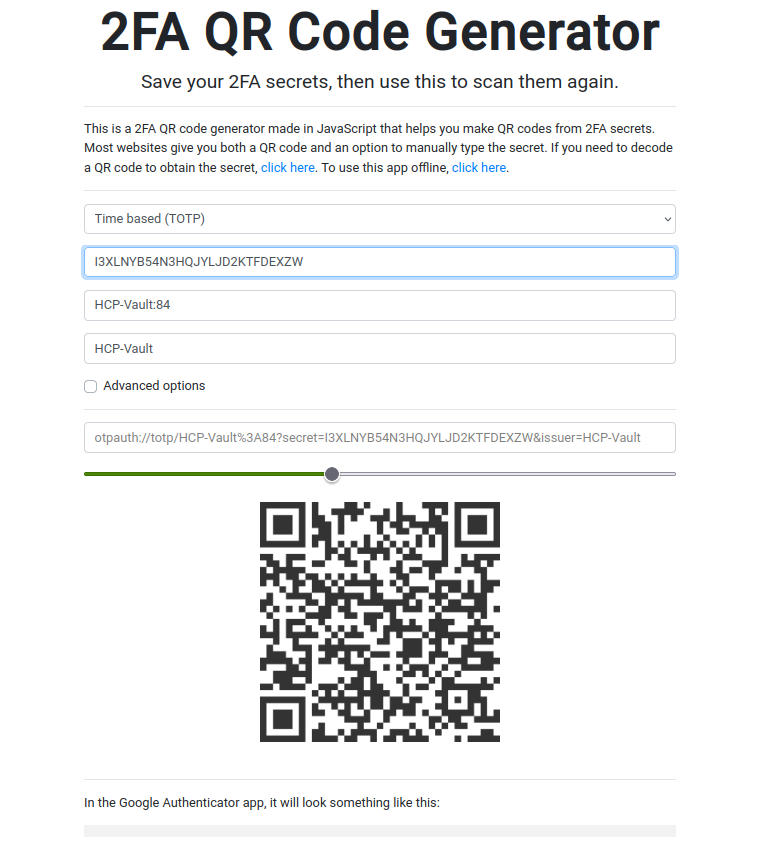
Scan the barcode using Google Authenticator or any compatible app.
Enforce MFA on Login:
vault write identity/mfa/login-enforcement/demo mfa_method_ids="$METHOD_ID" auth_method_accessors="$USERPASS_ACCESSOR"Now, Open the vault server using the browser and login with the user you have created, After entering the password it will ask you for the TOTP Passcode.
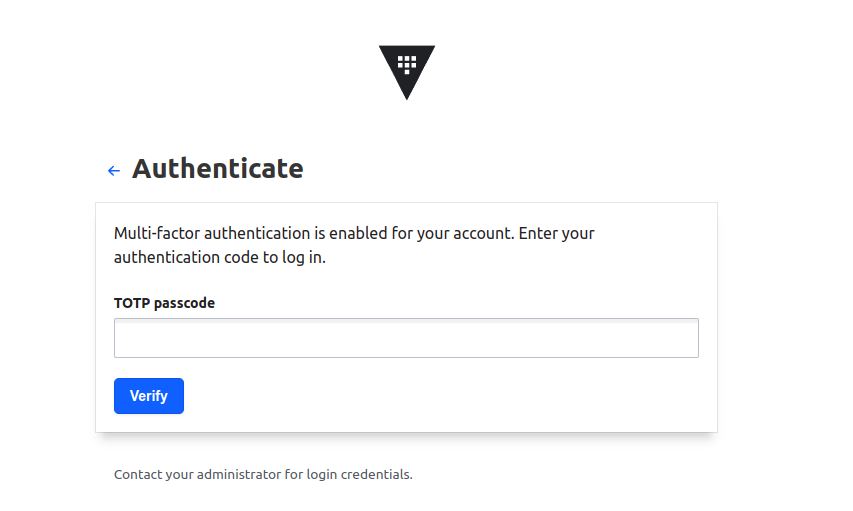
Open the authenticator app and update the code to login into the vault.
Enabling MFA for Existing Users
If you need to enable MFA for an existing user, follow these steps:
Retrieve the Userpass Auth Accessor:
USERPASS_ACCESSOR=$(vault auth list | grep userpass | awk '{print $3}')Get the Entity ID of the Existing User:
Replace EXISTING_USER with the username of the existing user:
ENTITY_ID=$(vault read -field=id identity/entity/name/EXISTING_USER)Create an Entity Alias:
vault write identity/entity-alias \
name=username \
canonical_id="$ENTITY_ID" \
mount_accessor="$USERPASS_ACCESSOR"Generate TOTP for the Existing User:
vault write identity/mfa/method/totp/admin-generate method_id=$METHOD_ID entity_id=$ENTITY_IDThis command will generate a barcode and URL. Use the URL to create a barcode.
Conclusion
By following these steps, you have successfully enabled Multi-Factor Authentication (MFA) using TOTP in HashiCorp Vault. This additional layer of security will help protect your Vault server from unauthorized access and enhance your overall security posture.
For more detailed information, refer to the HashiCorp Vault documentation
